As Philip II of Macedon said, “divide et impera," which can be translated into “divide and conquer." While this maxim was used in the context of human relationships, politics, and wars at that time, it also applies to many business scenarios like breaking a huge effort into multiple small tasks to streamline the total workload, reducing the size of large groups of people to become more agile, etc.
When it comes to managing the risks of using of open source, it is even more true as the primary user of insights may differ for security vulnerabilities (infosec and development teams), legal/license risk (legal and compliance teams) or technology obsolescence (development and maintenance teams).
Prioritization is also extremely important, especially when considering that many development teams are currently inundated – if not submerged – by information on open source vulnerabilities, licensing issues or deprecated components. While remediations are often a good course of action for an application, managers and executives may want to take a step back and rationalize time-intensive tasks. Taking into account, for instance, whether an application is publicly accessible or critical to the business helps make more informed decisions on how best to utilize limited resources for remediation.
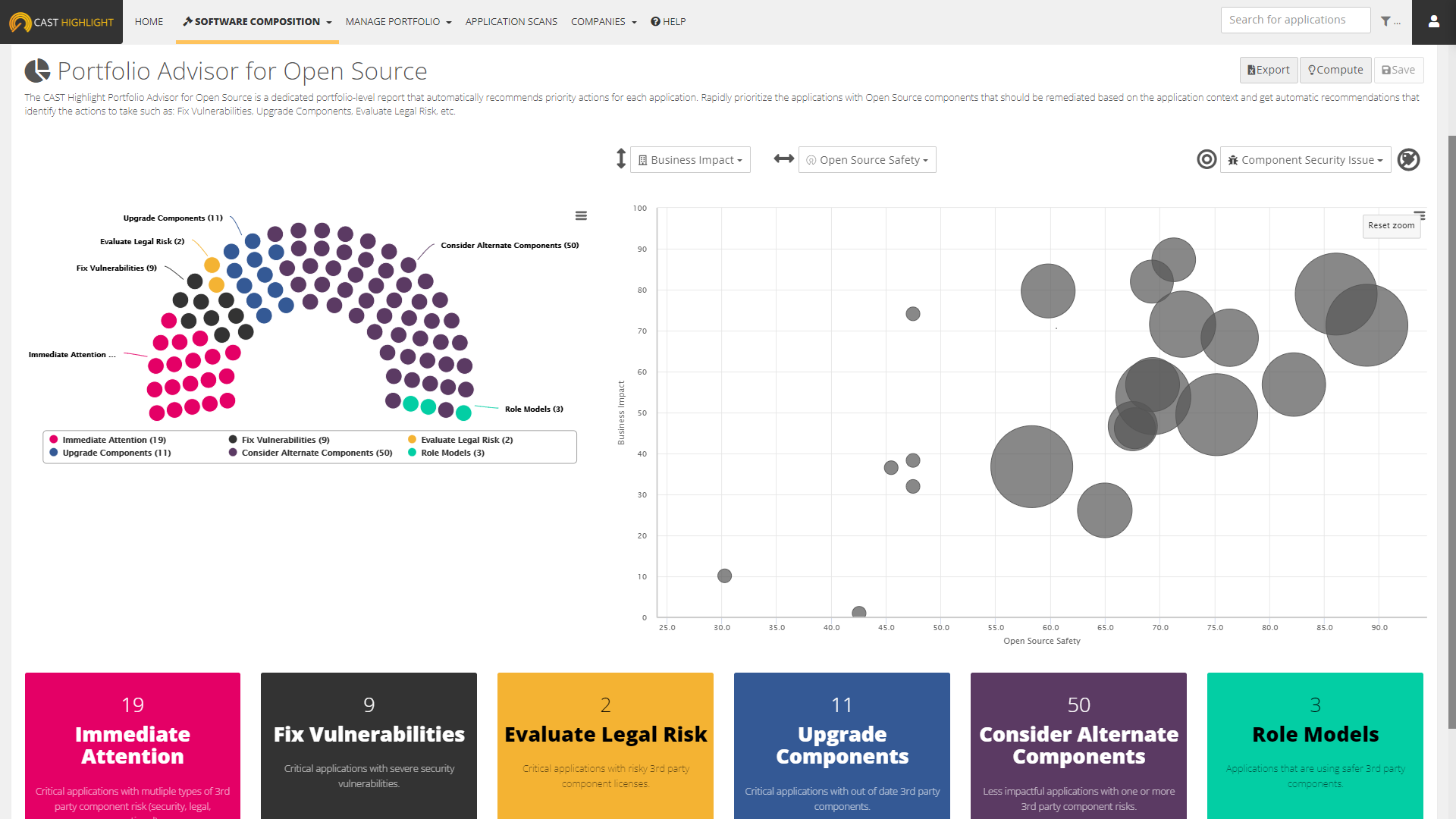
This is where CAST Highlight can help by using the new Portfolio Advisor for Open Source to automatically segment and prioritize your application portfolio with recommendations of the critical actions to take for each type of audience.
How CAST Highlight’s Portfolio Advisor for Open Source works
In CAST Highlight, we have developed a flexible and robust “Portfolio Advisor” foundational capability that is now progressively introduced in the product. Here is how it works.
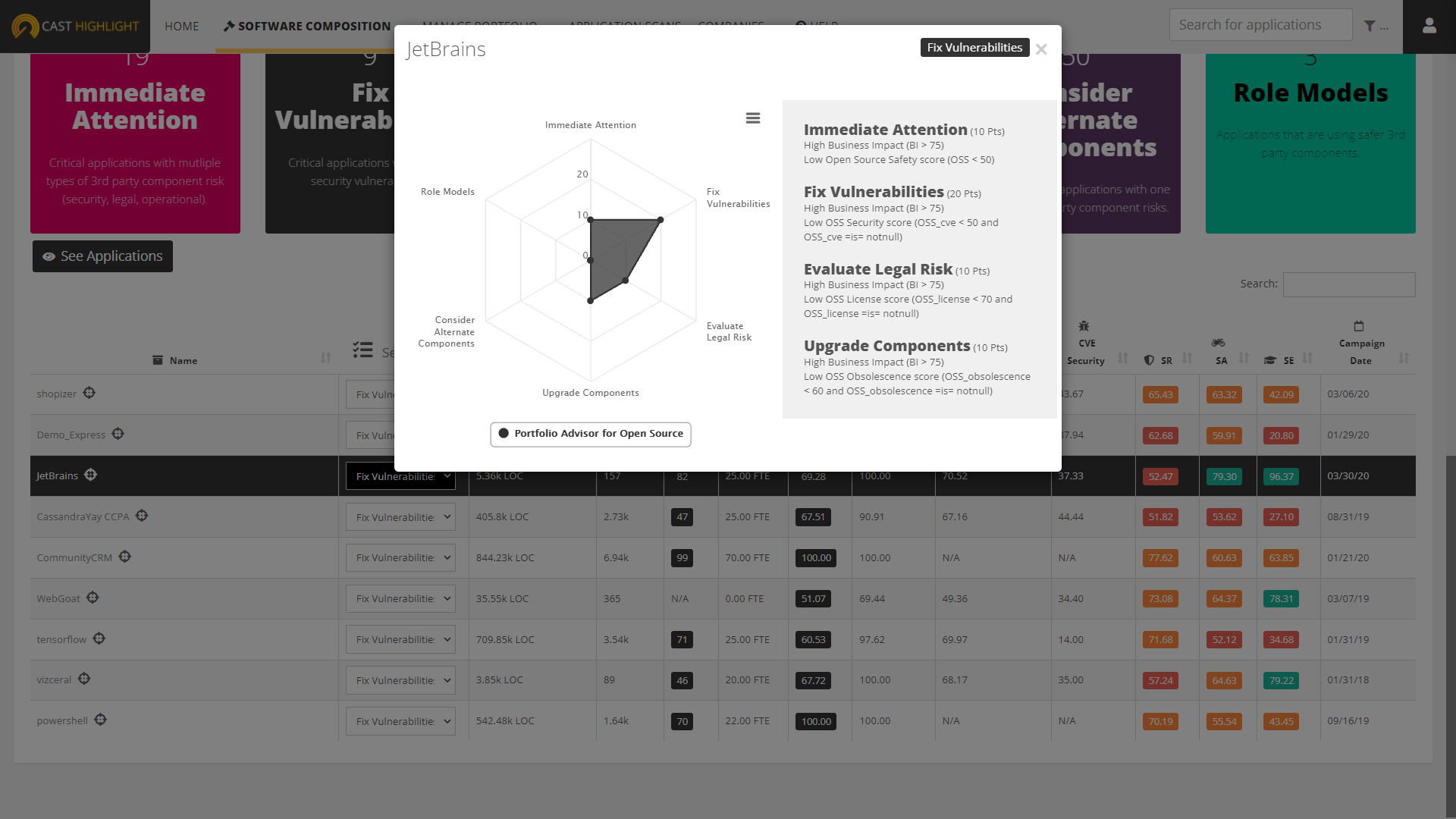
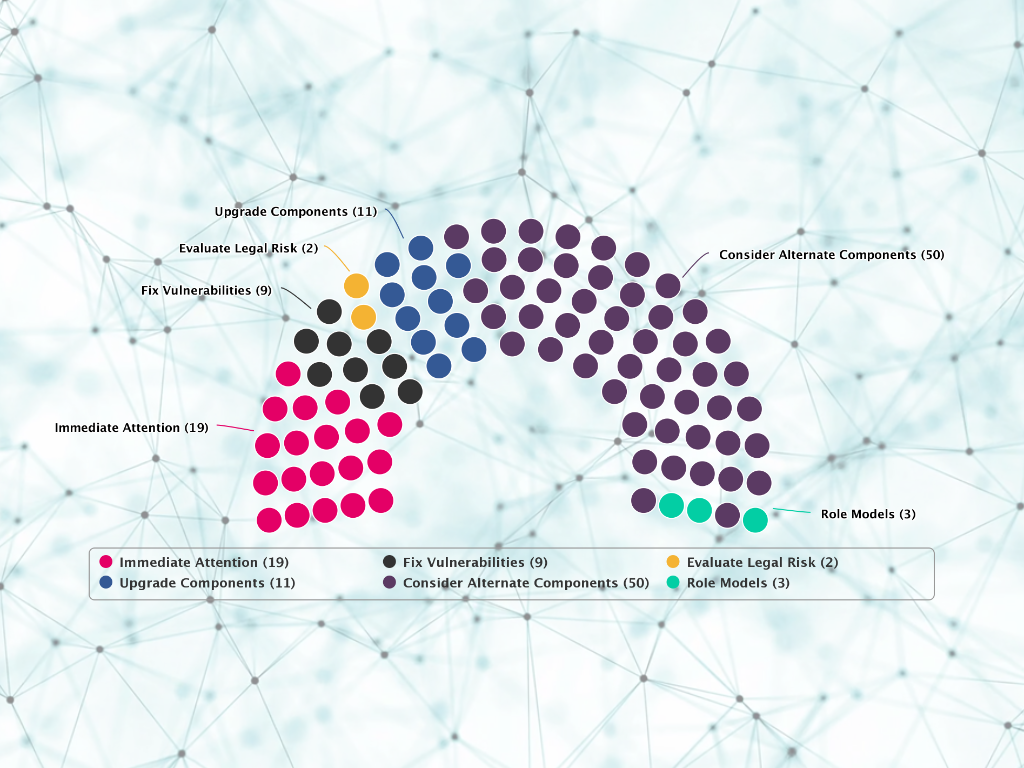
The six Portfolio Advisor for Open Source segments recommend specific actions to take on applications and are defined as follows:
- Immediate attention: These applications are important to the organization and have multiple 3rd party component risks which include two or more of the following: security vulnerabilities, risky licenses, obsolete components.
- Fix Vulnerabilities: These applications are important to the organization and are using 3rd party components that have critical or high severity security vulnerabilities.
- Evaluate Legal Risk: These applications are important to the organization and are using 3rd party components that have risky licenses.
- Upgrade Components: These applications are important to the organization and are using 3rd party components that are out of date or obsolete creating operational risk.
- Consider Alternate Components: These applications are less important to the organization and have multiple 3rd party component risks which include two or more of the following: security vulnerabilities, risky licenses, obsolete components.
- Role Models: These applications are using 3rd party components that have low risk for the organization
| Business Impact | Open Source Safety | OSS Security | OSS License | OSS Obsolescence | |
|---|---|---|---|---|---|
| Immediate Attention | High | Low | – | – | – |
| Fix Vulnerabilities | High | – | Low | – | – |
| Evaluate License Risk | High | – | – | Low | – |
| Component Upgrade | High | – | – | – | Low |
| Consider Alternate Components | Medium | Medium/Low | – | – | – |
| Role Models | – | High | – | – | – |
- Business Impact scores (from the Business Impact survey)
- Open Source Safety scores and benchmarks
- OSS Security scores (calculated from component vulnerability count by criticality)
- OSS License scores (calculated from component licenses and their corresponding level of compliance with the organization’s license policy)
- OSS Obsolescence scores (calculated from component version dates and gaps with the latest known versions)





SHARE